Sign in through Azure Active Directory federated identity provider
AWS side:
- Create the Cognito user pool
- Add a user pool domain name
- Add user pool’s app client
Azure side:
- Select Tenant
- Go to the Azure Active Directory
- Go to the Enterprise applications
- New application
- Create your own application
- Select: “Integrate any other application you don’t find in the gallery (Non-gallery)”
- Select: “Set up single sign on”
- SAML
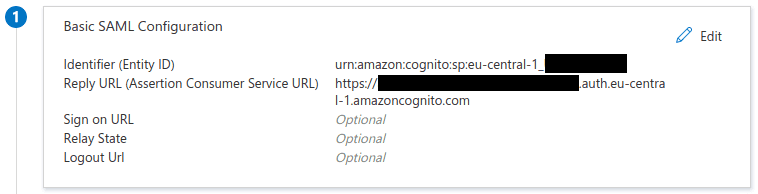
- Basic SAML configuration
Identifier (Entity ID): urn:amazon:cognito:sp:<COGNITO_USER_POOL_ID> Reply URL (Assertion Consumer Service URL): <user_pool_domain_name>
- Copy “App Federation Metadata Url”
- Add users/groups to the app
AWS side:
Identity providers
- Go to the Identity providers
- SAML
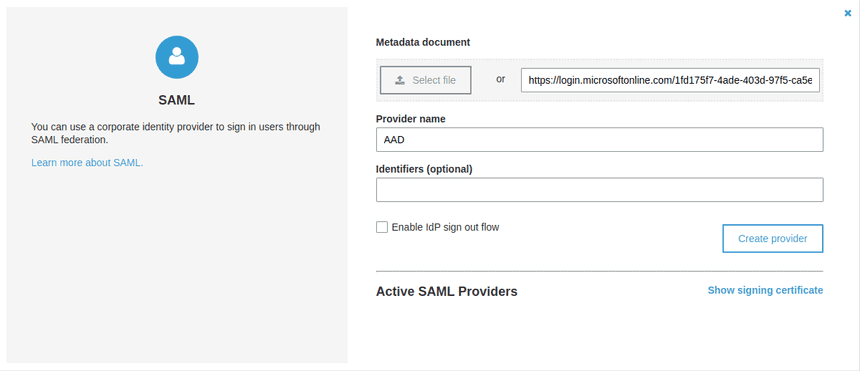
- SAML configuration
Metadata document: <app_federation_metadata_url>
Provider name: AADAttribute mapping
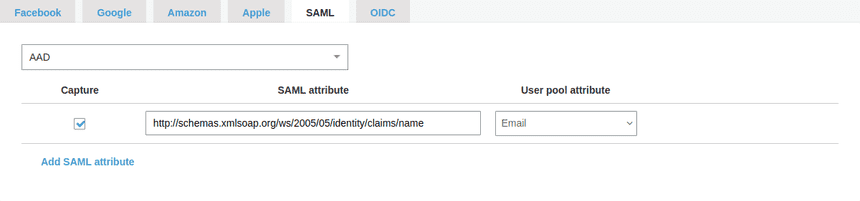
- Go to the Attribute mapping
- SAML, select “AAD” from the dropdown
- Add SAML attribute
Capture: true
SAML attribute: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
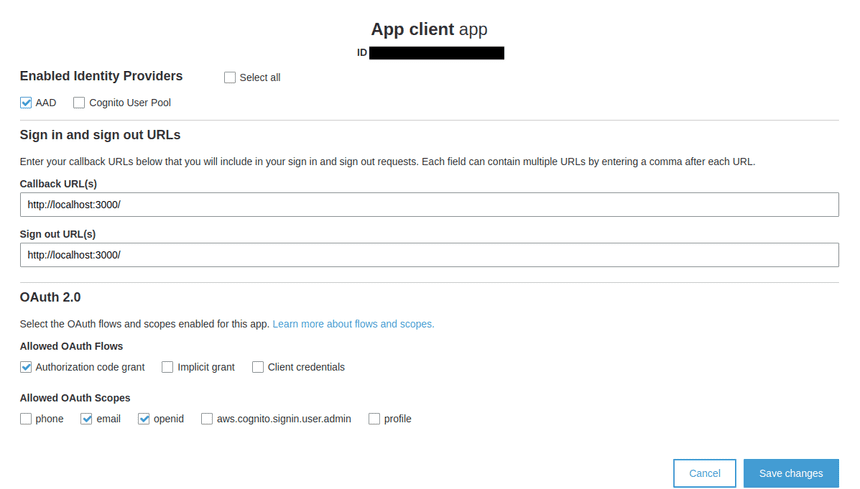
User pool attribute: EmailApp clients settings
Sign in via hosted UI. It should redirect you to the http://localhost:3000/?code=00000-00000-00000-00000.